What are Webhooks?
Webhooks are automated HTTP callbacks that allow Corgea to send real-time notifications to your external systems when specific events occur. Instead of continuously polling our API to check for updates, webhooks push event data directly to your specified endpoint the moment something happens.Key Benefits
- Real-time notifications - Receive instant updates when security issues are found, status changes occur, or scans complete
- Automation - Trigger workflows in external tools like Slack, Zapier, or custom applications
- Efficiency - No need to poll APIs - we push data to you when events happen
- Flexibility - Subscribe only to the events you care about and filter by project or status
- Reliability - Built-in retry logic and delivery tracking ensure your notifications get through
Supported Event Types
Corgea supports webhooks for the following events: Issue Events:issue.status_changed- Triggered when an issue’s status is updated (e.g., open → fixed)issue.assigned- Triggered when an issue is assigned to a team member
scan.started- Triggered when a security scan beginsscan.completed- Triggered when a scan finishes successfullyscan.failed- Triggered when a scan encounters an error
How Webhooks Work
The Webhook Lifecycle
Event Occurs
Webhook Triggered
Filtering Applied
Payload Built
HTTP POST Request
Retry Logic
Delivery Logged
Payload Structure
All webhook payloads follow a standardized structure:Security Features
HMAC Signature Verification
HMAC Signature Verification
- When you provide a secret key, Corgea includes an
X-Corgea-Signatureheader - This header contains an HMAC-SHA256 hash of the payload
- Verify the signature to ensure the webhook came from Corgea
Custom Headers
Custom Headers
- Include headers required by your endpoint (e.g., authentication tokens)
- Configure custom headers during webhook setup
HTTPS Required
HTTPS Required
- All webhook URLs must use HTTPS for secure transmission
- Non-HTTPS URLs will be rejected to protect sensitive data
Automatic Retry Logic
- Initial attempt + 2 retries = 3 total attempts
- Exponential backoff: 2 seconds, 4 seconds between retries
- Timeout: 10 seconds per request
- Auto-pause: After 10 consecutive failures, the webhook is automatically paused
Headers Sent with Each Webhook
Setting Up a Webhook
Prerequisites
Step-by-Step Setup
Navigate to Integrations
- Go to your Corgea dashboard
- Click on “Integrations” in the navigation menu
- Select “Webhooks” or “Create New Webhook”
Configure Basic Settings
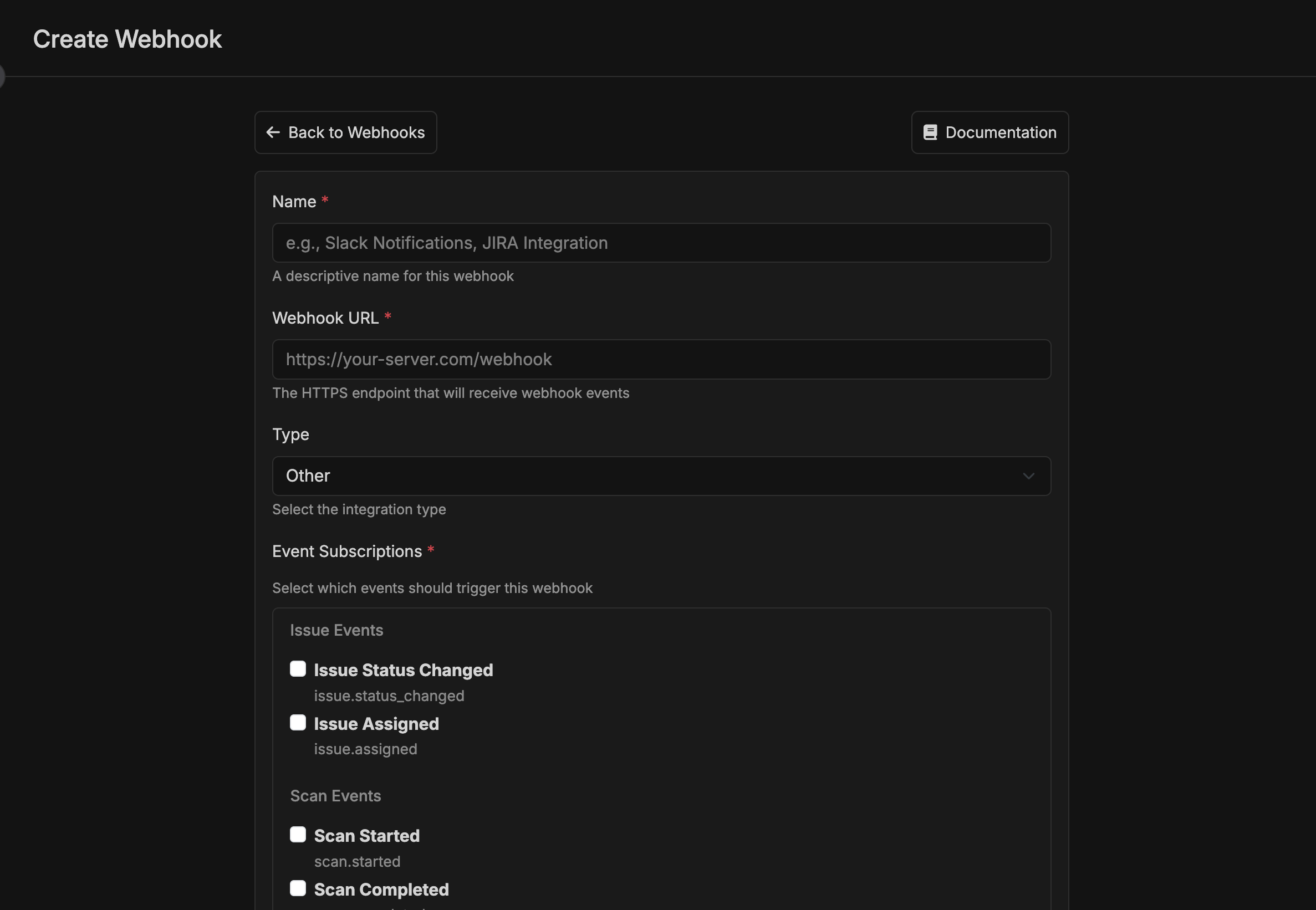
- Name: Give your webhook a descriptive name (e.g., “Slack Notifications”, “Production Scan Alerts”)
- Webhook URL: Enter your HTTPS endpoint URL
- Type: Select the integration type:
Slack- For Slack webhook integrationsZapier- For Zapier zapsOther- For custom integrations
Subscribe to Events
- Check the boxes for events you want to receive:
- Issue Status Changed
- Issue Assigned
- Scan Started
- Scan Completed
- Scan Failed
- You can select multiple events per webhook
Configure Filters (Optional)
- Leave empty to receive events from all projects
- Select specific projects to only receive their events
- Useful for routing different projects to different endpoints
issue.status_changed events)- Leave empty to receive all status changes
- Select specific statuses (e.g.,
fixed,false_positive) to only receive those changes - Reduces noise by filtering out irrelevant status updates
Add Security (Optional but Recommended)
- Enter a random, secure string (minimum 32 characters recommended)
- Corgea will include an HMAC signature in the
X-Corgea-Signatureheader - Use this to verify webhook authenticity on your end
- Add any headers your endpoint requires
- Common examples:
Authorization: Bearer <token>,X-API-Key: <key>
Test Your Webhook
- Click “Test Webhook” to send a sample payload
- Verify your endpoint receives and processes the test correctly
- Check the response status and any error messages
Save and Activate
- Click “Create Webhook” or “Save”
- The webhook is now active and will start receiving events
Verifying Webhook Signatures
- Python
- Node.js
Use Cases
1. Real-time Slack Notifications
Scenario: Notify your security team in Slack when high-severity issues are found Setup:- Create a Slack incoming webhook URL in your Slack workspace
- In Corgea, create a webhook with:
- Type:
Slack - URL: Your Slack webhook URL
- Events:
scan.completed - Project Filter: Critical production projects
- Type:
2. Automated Ticketing for Critical Issues
Scenario: Automatically create tickets in Jira/Linear when critical issues are detected Setup:- Create a Zapier zap or custom endpoint that creates tickets
- In Corgea, create a webhook with:
- Events:
scan.completed,issue.status_changed - Status Filter: Only
openstatus (to avoid duplicate tickets) - Project Filter: Production projects
- Events:
3. Risk Acceptance Workflow Integration
Scenario: Automatically document accepted risks in Jira or Linear when security issues are marked as “Accepted Risk” Setup:- Create an endpoint or Zapier integration that creates documentation tickets
- In Corgea, create a webhook with:
- Events:
issue.status_changed - Status Filter: Only
accepted_riskstatus - Project Filter: All projects or specific high-compliance projects
- Events:
- Configure the integration to:
- Create a ticket documenting the risk acceptance
- Include issue details (classification, file path, urgency)
- Tag with “risk-acceptance” label
- Assign to security lead for review
4. Custom Dashboard Integration
Scenario: Display real-time security metrics on your internal dashboard Setup:- Build an endpoint that receives webhook data and updates your dashboard
- In Corgea, create a webhook with:
- Events: All scan and issue events
- No filters (receive everything)
5. Multi-team Routing
Scenario: Route different project notifications to different teams Setup:- Create separate webhooks for each team:
- Backend Team Webhook: Project filter = backend projects, Slack channel #backend-security
- Frontend Team Webhook: Project filter = frontend projects, Slack channel #frontend-security
- DevOps Team Webhook: Project filter = infrastructure projects, Slack channel #devops-security
6. Compliance Reporting
Scenario: Automatically log all security findings to a compliance system Setup:- Create an endpoint that writes to your compliance database
- In Corgea, create a webhook with:
- Events:
scan.completed - All projects
- Store webhook delivery history for audit trail
- Events:
Troubleshooting
Viewing Webhook Delivery History
Navigate to Webhook History
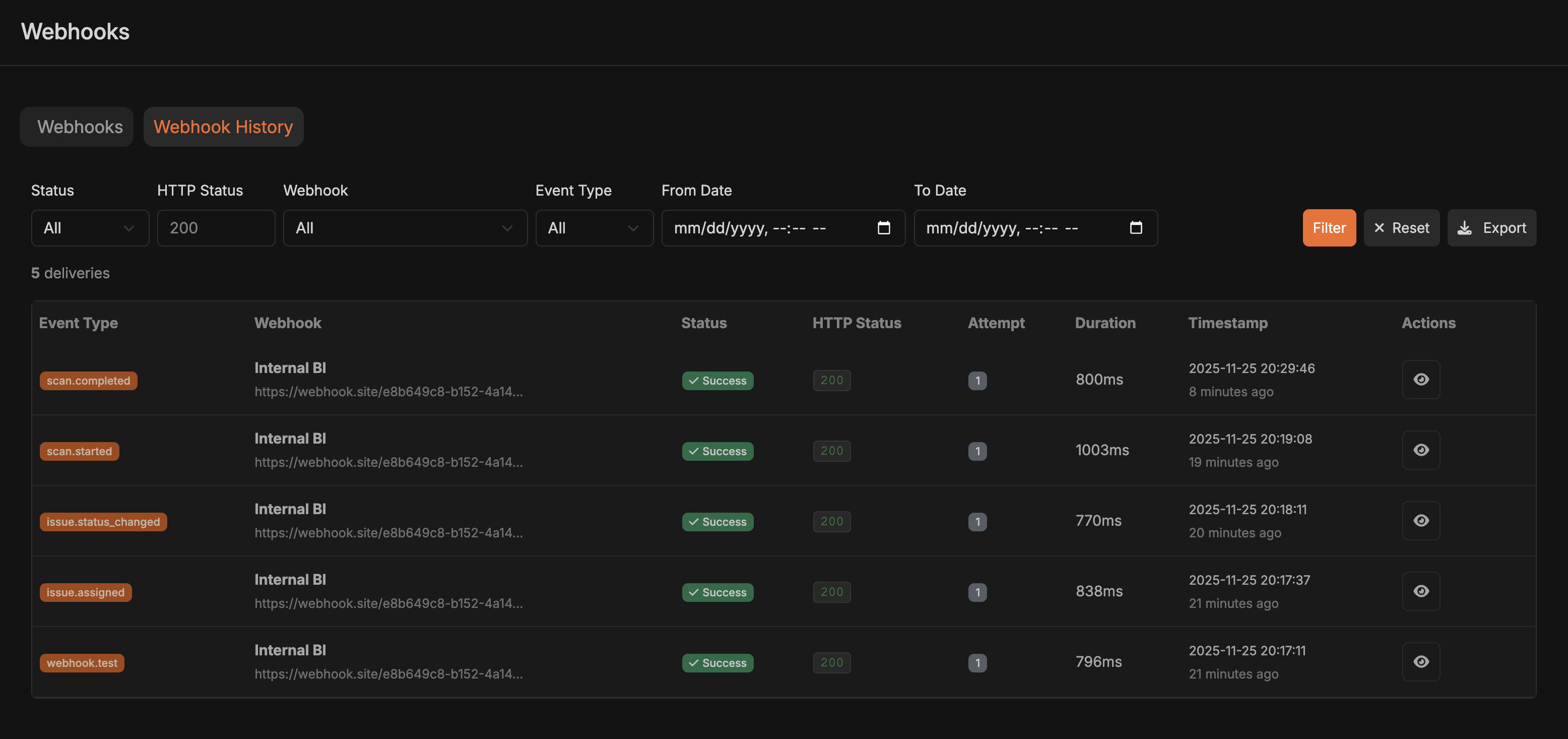
Access Delivery Log
Review Delivery Details
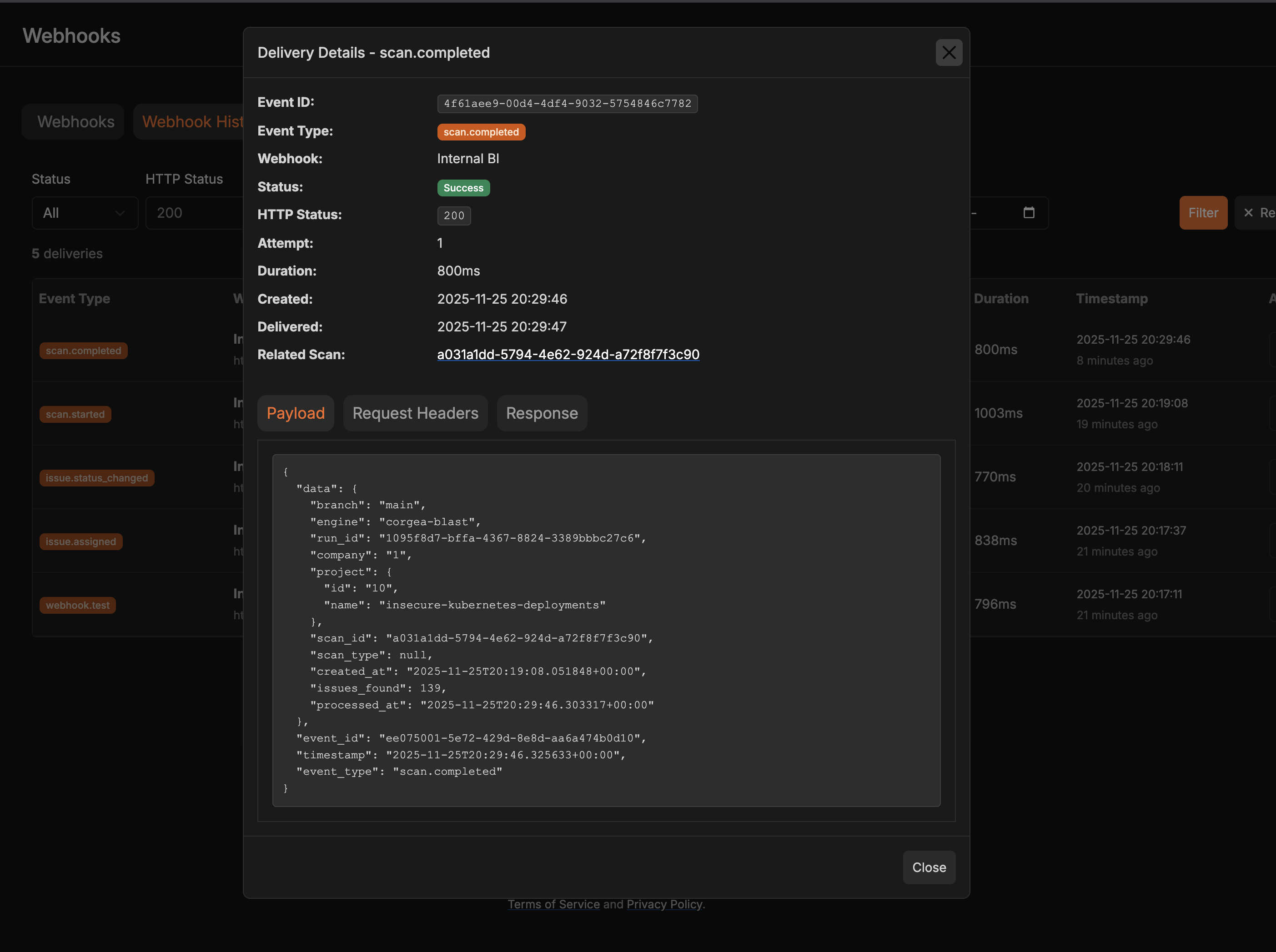
- Event type and timestamp
- HTTP status code
- Request/response details
- Error messages (if any)
- Retry attempts
Common Issues and Solutions
Webhook Not Receiving Events
Webhook Not Receiving Events
- Webhook is paused or inactive
- Event subscriptions not configured
- Project/status filters excluding events
- Endpoint not returning 2xx status codes
- Check webhook status - ensure it’s active (not paused)
- Verify event subscriptions are selected
- Review filters - temporarily remove filters to test
- Check your endpoint logs for incoming requests
- Test the webhook using the “Test Webhook” button
Webhook Automatically Paused
Webhook Automatically Paused
- Check the delivery history for error details
- Verify your endpoint URL is correct and accessible
- Ensure your endpoint returns 2xx status codes
- Check for firewall/security rules blocking Corgea’s requests
- Fix the underlying issue, then manually re-activate the webhook
- Use “Test Webhook” to verify it’s working before re-enabling
Receiving Too Many Webhook Calls
Receiving Too Many Webhook Calls
- Use Status Filters: For
issue.status_changed, filter to only statuses you care about (e.g., onlyfixedandfalse_positive) - Use Project Filters: Only subscribe to specific critical projects
- Reduce Event Subscriptions: Unsubscribe from events you don’t need
- Implement Rate Limiting: On your endpoint, implement rate limiting or queuing
Signature Verification Failing
Signature Verification Failing
- Wrong secret key
- Incorrect signature verification logic
- Character encoding issues
- Verify you’re using the exact secret key from Corgea
- Ensure you’re using HMAC-SHA256 algorithm
- Use the raw request body (not parsed JSON) for verification
- Check for UTF-8 encoding on both sides
- Use
hmac.compare_digest()(Python) orcrypto.timingSafeEqual()(Node.js) for timing-safe comparison
Endpoint Timing Out
Endpoint Timing Out
- Acknowledge Immediately: Return 200 OK immediately, then process asynchronously
- Use a Queue: Add webhook payloads to a queue for background processing
- Optimize Processing: Speed up your webhook handler logic
- Increase Resources: Scale up your endpoint infrastructure
Duplicate Events
Duplicate Events
- Multiple webhooks subscribed to same event
- Retry logic triggering after delayed success
- Check for duplicate webhook configurations
- Use
event_idfield for idempotency - store processed event IDs and skip duplicates - Implement idempotency keys in your endpoint
Missing Data in Payload
Missing Data in Payload
- Check the webhook delivery history for the full payload
- Some fields may be
nullif data doesn’t exist (e.g., unassigned issues) - Implement null checks in your handler code
- Reference the event-specific payload structure in the delivery history
Getting Webhook Statistics
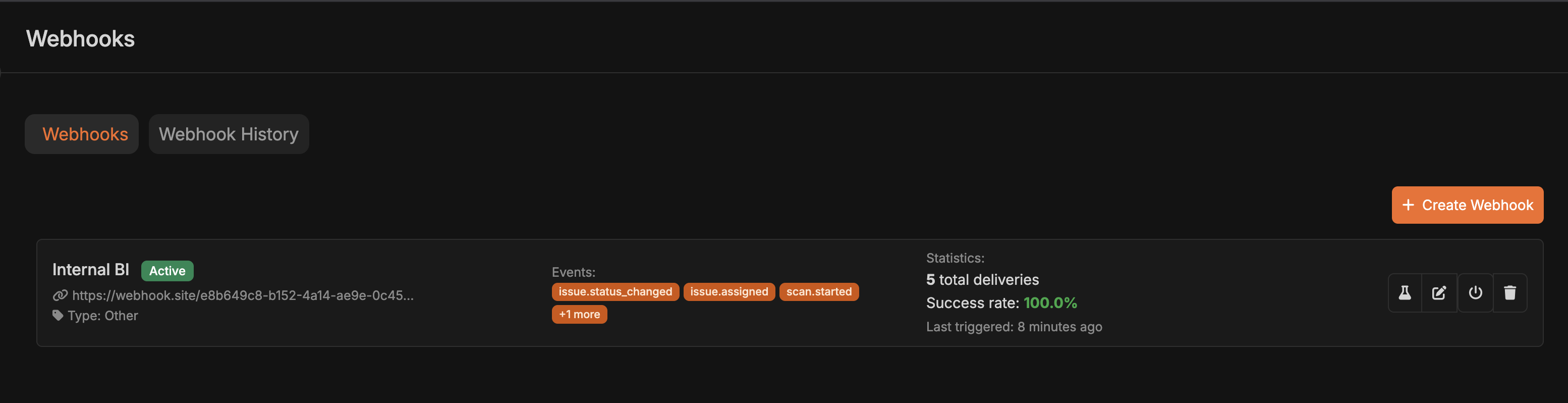
View performance metrics for your webhooks:- Navigate to Integrations → Webhooks
- View each webhook’s statistics:
- Total Deliveries: Total number of webhook calls
- Successful Deliveries: Calls that returned 2xx
- Failed Deliveries: Calls that failed or timed out
- Success Rate: Percentage of successful deliveries
- Consecutive Failures: Current failure streak
- Last Triggered: When the webhook last fired
Manual Retry
If a webhook delivery failed, you can manually retry it:- Go to Integrations → Webhooks → History
- Find the failed delivery
- Click Retry
- A new delivery attempt will be created and sent immediately
Exporting Delivery History
For compliance or debugging, export webhook delivery history:- Navigate to Integrations → Webhooks → History
- Apply filters (date range, event type, status, webhook)
- Click Export to download CSV
- Use the export for:
- Compliance audits
- Performance analysis
- Debugging patterns
- Issue resolution tracking
Testing Tips
Before Going Live
Before Going Live
- Use webhook.site or RequestBin to inspect payloads
- Test with low-volume projects first
- Monitor delivery success rate for the first few days
- Set up alerting for webhook failures in your own system
Debug Checklist
Debug Checklist
- Webhook URL is correct and accessible
- Endpoint returns 2xx status code within 10 seconds
- Firewall allows Corgea’s requests
- Event subscriptions are selected
- Filters are configured correctly (or removed for testing)
- Signature verification works (if using secret)
- Webhook is active (not paused)
Payload Examples
- Issue Status Changed
- Scan Completed
- Issue Assigned
FAQ
Can I use the same webhook URL for multiple event types?
Can I use the same webhook URL for multiple event types?
X-Corgea-Event header and event_type field to identify the event.How many webhooks can I create?
How many webhooks can I create?
What happens if my endpoint is down?
What happens if my endpoint is down?
Can I test webhooks without triggering real events?
Can I test webhooks without triggering real events?
Do webhooks support authentication?
Do webhooks support authentication?
Can I filter webhooks to specific branches?
Can I filter webhooks to specific branches?
Are webhook payloads encrypted?
Are webhook payloads encrypted?
How long are webhook delivery logs kept?
How long are webhook delivery logs kept?
Can I retry a webhook manually?
Can I retry a webhook manually?
What IP addresses does Corgea send webhooks from?
What IP addresses does Corgea send webhooks from?
Questions or issues? Contact Corgea Support
